INSTALL FRIDA OBJECTION
To install Frida and its associated tools, you can follow these step-by-step instructions:
Frida requires Python to be installed on your system. You can download and install Python from the official Python website https://www.python.org Make sure to choose the appropriate version for your operating system.
Start Cydia and add Frida repository by going to Manage -> Sources -> Edit -> Add and enter https://build.frida.re. You should now be able to find and install the Frida package which lets Frida inject JavaScript into apps running on your iOS device. This happens over USB, so you will need to have your USB cable handy, though there no need to plug it in just yet.
You can use PID or Bundle ID to lauch app and attach it.
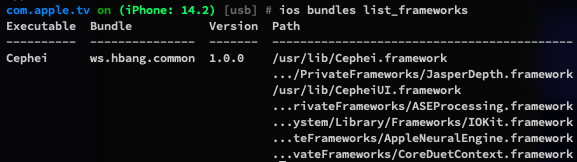
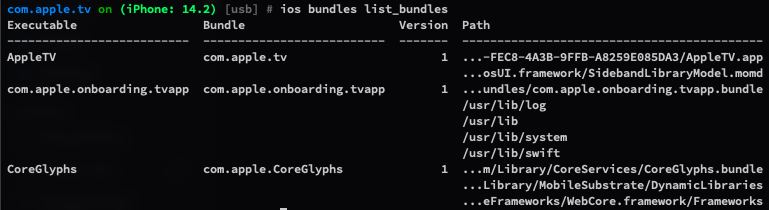
Use ios bundles to list app frameworks and bundles.
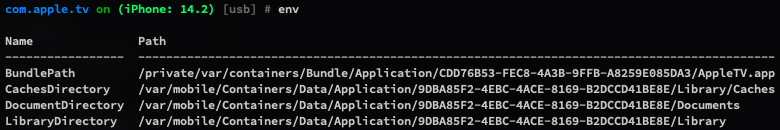
You can use ls command to list files in app directory, and you can use cd command to check working directory
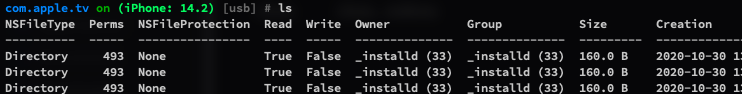
You can use file cat command to view file content.
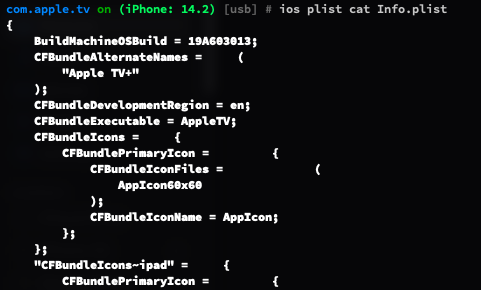
You can use for plist type file, can also use ios plist cat "plist file path" to decode plist file.
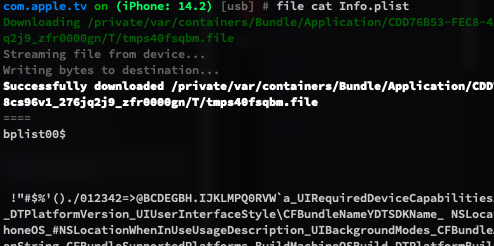
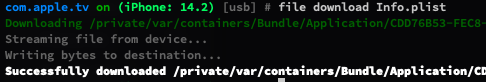
You can use file download "file path" to download a file from device.
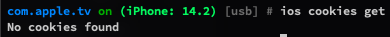
You can use ios cookies get to get cookies.
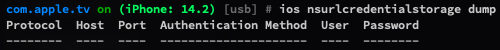
You can use ios nsurlcredentialstorage dump to dump all of the credentials in the shared NSURLCredentialStorage.
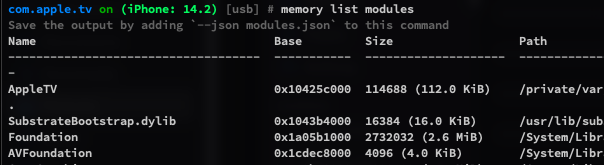
You can use memory list modules to list all the loaded modules in the current process.
You can use memory dump all "output file path" to dump app memory to.
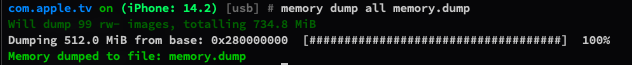
After dump memory, you can use strings to check readable strings in memory,
You can use memory dump all "output file path" to dump app memory to.
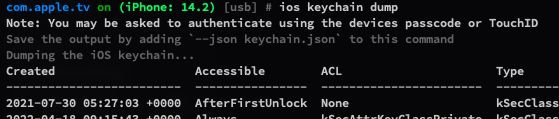
Using ios keychain.
You can use ios pasteboard monitor to monitor the iOS pasteboard.
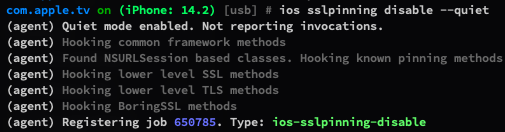
Objection is our best recommendation and first approach to remove certificate pinning on iOS.